This blog address :https://blog.csdn.net/wutianxu123/article/details/125397313
When a certain computer in the Intranet can be accessed remotely SSH Server time , If the purpose at this time is to set up an intranet web The server , When you can't access that web The server , And this one is accessible SSH There are no tools installed on the server , We can configure a reverse line SSH Tunnel connection ( without SSH service ).
To build such a tunnel , Must first be as usual , From intranet Windows The client is connected to the Internet SSH Server . Through this article SSH Connect , We can build a tunnel between a remote port and a local port on the server . Through this local port , We can expose the... Of an internal system 3389 Port and access through remote desktop protocol , Or visit this Windows Any system that the device can access .
Paramiko In the official example of rforward.py Program , Position in :paramiko-main\demos\rforward.py, You can use it directly .
The core part has been annotated in Chinese . The code is as follows :
#!/usr/bin/python
#-*- coding:utf8 -*-
import getpass
import os
import socket
import select
import sys
import threading
from optparse import OptionParser
import paramiko
SSH_PORT = 22
DEFAULT_PORT = 4000
g_verbose = True
# Manage the communication of each thread
def handler(chan, host, port):
sock = socket.socket()
try:
sock.connect((host, port))
except Exception as e:
verbose("Forwarding request to %s:%d failed: %r" % (host, port, e))
return
verbose(
"Connected! Tunnel open %r -> %r -> %r"
% (chan.origin_addr, chan.getpeername(), (host, port))
)
# Complete data sending and receiving
while True:
r, w, x = select.select([sock, chan], [], [])
if sock in r:
data = sock.recv(1024)
if len(data) == 0:
break
chan.send(data)
if chan in r:
data = chan.recv(1024)
if len(data) == 0:
break
sock.send(data)
chan.close()
sock.close()
verbose("Tunnel closed from %r" % (chan.origin_addr,))
def reverse_forward_tunnel(server_port, remote_host, remote_port, transport):
# transport Responsible for establishing and maintaining encrypted communications
# request_port_forward Set a port on the server TCP All connections are forwarded
transport.request_port_forward("", server_port)
while True:
# channel encryption transport Data sent and received in the session
# Build a new one channel
chan = transport.accept(1000)
if chan is None:
continue
# call handler Function handles this channel
thr = threading.Thread(
target=handler, args=(chan, remote_host, remote_port)
)
thr.setDaemon(True)
thr.start()
def verbose(s):
if g_verbose:
print(s)
HELP = """\ Set up a reverse forwarding tunnel across an SSH server, using paramiko. A port on the SSH server (given with -p) is forwarded across an SSH session back to the local machine, and out to a remote site reachable from this network. This is similar to the openssh -R option. """
def get_host_port(spec, default_port):
"parse 'hostname:22' into a host and port, with the port optional"
args = (spec.split(":", 1) + [default_port])[:2]
args[1] = int(args[1])
return args[0], args[1]
# Parameter declarations
def parse_options():
global g_verbose
parser = OptionParser(
usage="usage: %prog [options] <ssh-server>[:<server-port>]",
version="%prog 1.0",
description=HELP,
)
parser.add_option(
"-q",
"--quiet",
action="store_false",
dest="verbose",
default=True,
help="squelch all informational output",
)
parser.add_option(
"-p",
"--remote-port",
action="store",
type="int",
dest="port",
default=DEFAULT_PORT,
help="port on server to forward (default: %d)" % DEFAULT_PORT,
)
parser.add_option(
"-u",
"--user",
action="store",
type="string",
dest="user",
default=getpass.getuser(),
help="username for SSH authentication (default: %s)"
% getpass.getuser(),
)
parser.add_option(
"-K",
"--key",
action="store",
type="string",
dest="keyfile",
default=None,
help="private key file to use for SSH authentication",
)
parser.add_option(
"",
"--no-key",
action="store_false",
dest="look_for_keys",
default=True,
help="don't look for or use a private key file",
)
parser.add_option(
"-P",
"--password",
action="store_true",
dest="readpass",
default=False,
help="read password (for key or password auth) from stdin",
)
parser.add_option(
"-r",
"--remote",
action="store",
type="string",
dest="remote",
default=None,
metavar="host:port",
help="remote host and port to forward to",
)
options, args = parser.parse_args()
if len(args) != 1:
parser.error("Incorrect number of arguments.")
if options.remote is None:
parser.error("Remote address required (-r).")
g_verbose = options.verbose
server_host, server_port = get_host_port(args[0], SSH_PORT)
remote_host, remote_port = get_host_port(options.remote, SSH_PORT)
return options, (server_host, server_port), (remote_host, remote_port)
def main():
# It will check whether the required parameters have been passed in
options, server, remote = parse_options()
password = None
if options.readpass:
password = getpass.getpass("Enter SSH password: ")
# Create a Paramiko Of SSH Client connection
client = paramiko.SSHClient()
client.load_system_host_keys()
client.set_missing_host_key_policy(paramiko.WarningPolicy())
verbose("Connecting to ssh host %s:%d ..." % (server[0], server[1]))
try:
client.connect(
server[0],
server[1],
username=options.user,
key_filename=options.keyfile,
look_for_keys=options.look_for_keys,
password=password,
)
except Exception as e:
print("*** Failed to connect to %s:%d: %r" % (server[0], server[1], e))
sys.exit(1)
verbose(
"Now forwarding remote port %d to %s:%d ..."
% (options.port, remote[0], remote[1])
)
try:
reverse_forward_tunnel(
options.port, remote[0], remote[1], client.get_transport()
)
except KeyboardInterrupt:
print("C-c: Port forwarding stopped.")
sys.exit(0)
if __name__ == "__main__":
main()
command :
python rforward.py 192.168.153.141 -p 8081 -r 192.168.153.140:3000 --user=kali --password
remarks :
192.168.153.141, yes SSH Server's IP
192.168.153.140, yes web Server's IP
--user, yes SSH User name of the server
--password, yes SSH The password of the server
Running effect :
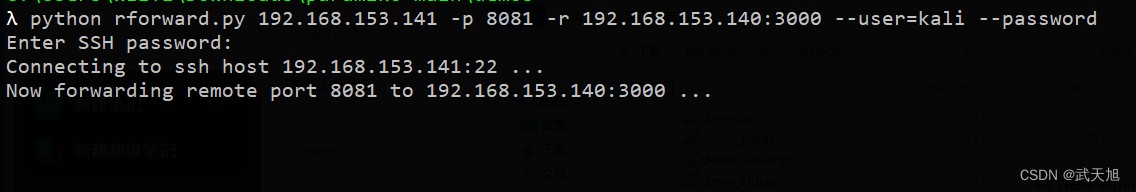
We are connected to SSH The server , And opened it on top 8081 port , This port will forward traffic to web Server's 3000 On port , Now in SSH Access on the server http://127.0.0.1:8081, Will pass SSH The tunnel is connected to a tunnel located at web On the server 3000 On port web service .