Resource download address :https://download.csdn.net/download/sheziqiong/85730749
Resource download address :https://download.csdn.net/download/sheziqiong/85730749
Catalog
Chapter one Demand analysis 1
1.1 Research background and significance 1
1.2 Related research status and development trend at home and abroad 1
1.3 The full text is arranged 2
Chapter two DES Algorithm principle 3
2.1 DES brief introduction 3
2.2 DES Encryption and decryption of 3
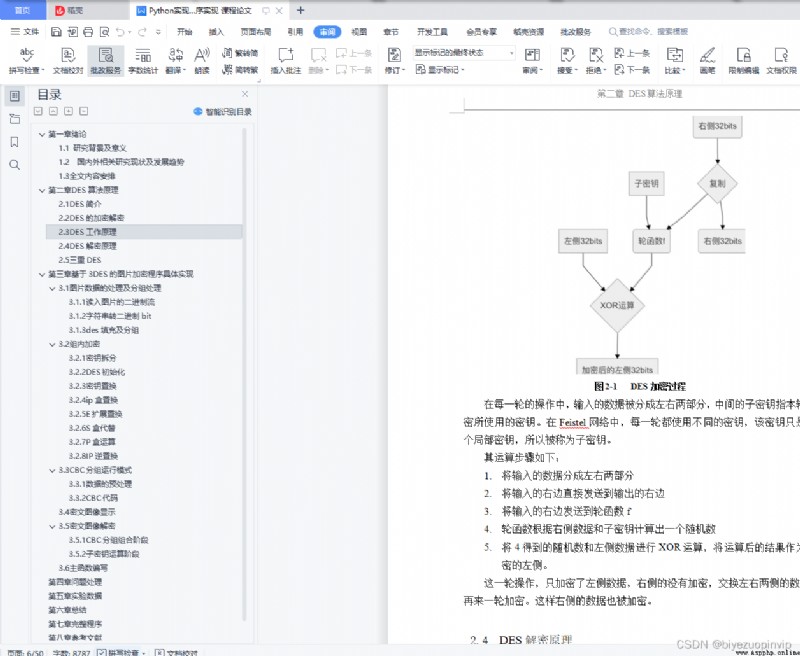
2.3 DES working principle 3
2.4 DES Decryption principle 4
2.5 triple DES 5
The third chapter be based on 3DES Image encryption program specific implementation 6
3.1 Processing and grouping of picture data 6
3.1.1 Read in the binary stream of the picture 6
3.1.2 String to binary bit 6
3.1.3 des Filling and grouping 7
3.2 Intra group encryption 8
3.2.1 Key splitting 8
3.2.2 DES initialization 10
3.2.3 Key exchange 10
3.2.4 ip Box of replacement 12
3.2.5 E Extended displacement 14
3.2.6 S Box replacement 14
3.2.7 P Box operation 15
3.2.8 IP Reverse displacement 16
3.3 CBC Group operation mode 16
3.3.1 Data preprocessing 17
3.3.2 CBC Code 18
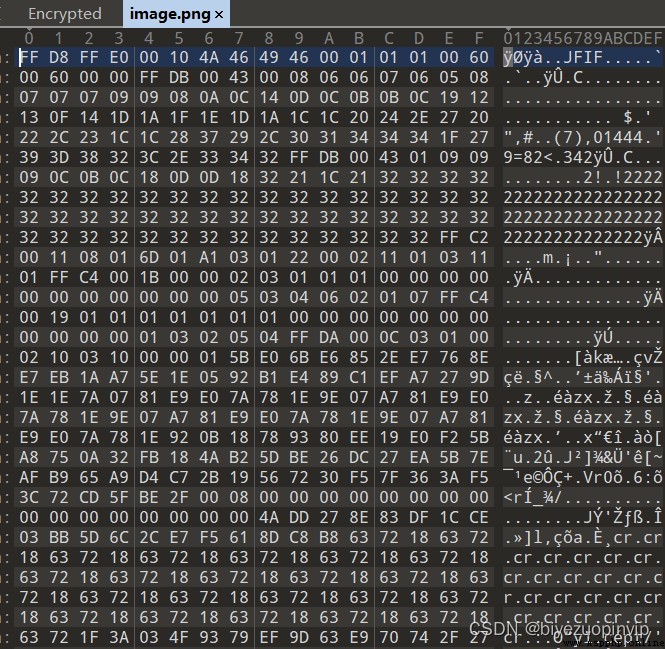
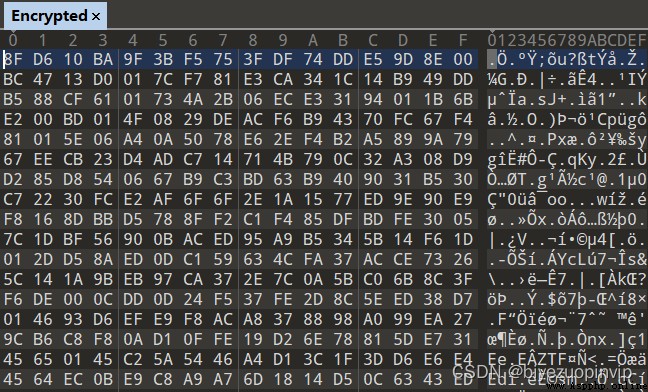
3.4 Ciphertext image display 19
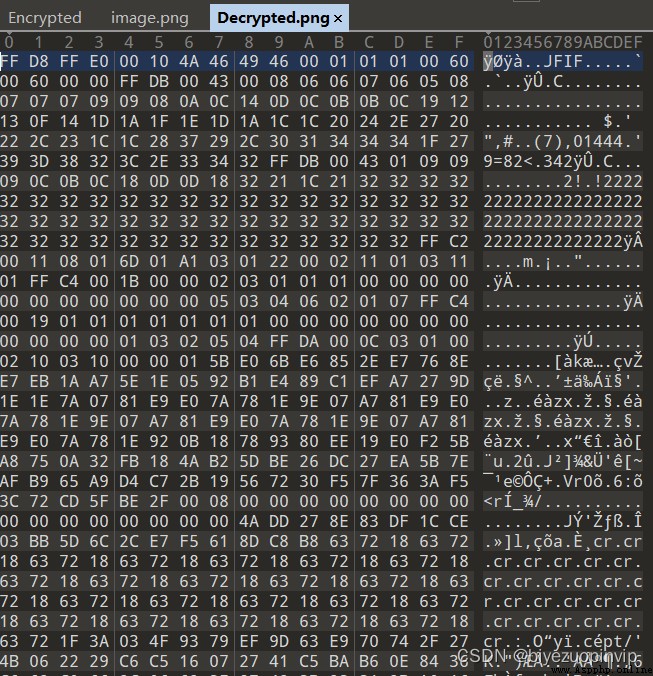
3.5 Ciphertext image decryption 21
3.5.1 CBC Grouping and combination stage 21
3.5.2 Subkey operation stage 21
3.6 Write the main function 22
Chapter four Problem handling 25
The fifth chapter experimental data 26
Chapter six summary 28
Chapter vii. The whole program 29
Chapter viii. reference 48
The first chapter is introduction
This chapter is the introduction of the whole article , First described DES The overall research background of the algorithm and the great significance of encryption technology are discussed ; Secondly, after reading a large number of Chinese and English literature, I will focus on the current domestic and international research on DES The research status of application is summarized ; Finally, it summarizes the main research work of this paper and the structure of the whole paper .
1.1 Research background and significance
With the rapid development and wide application of information and communication technology , Network and information system fundamentals 、 The role of the overall situation is growing , People exchange information through the Internet , It is hard to avoid password protection , This is not only related to personal privacy, but also may be a state secret , National security . The security and protection of privacy and confidential network information has increasingly become a key problem to be solved . In that sense , This paper presents an effective encryption algorithm for passwords , Is the problem we must face , But the complexity and disorder of the password bring difficulties to the design of the encryption algorithm , therefore , We must find a regular algorithm that is generally applicable to simple ciphers , that , The encryption of symmetric passwords has become the most practical and common problem . With the development of China's economy , The development and rise of society , The convenience and quickness of life are more and more popular , Online shopping , Online trade fairs are becoming more and more frequent , In this way , Password security has become our most concerned problem . Password protection has become our consensus and demand , Encryption can best reflect its weight , That pair of symmetry
The encryption of password also has far-reaching research value and practical significance .
Not only at home , Foreign countries also attach importance to data encryption ,1977 year , American data encryption standard (Data Encryption Standard, DES) To enact , Thereafter 30 year ,DES Become a worldwide standard ,, Continuous improvement of relevant algorithms , And new methods , The constant emergence of new ideas , these , It plays a great role in the in-depth study of symmetric cryptographic algorithms .
1.2 Related research status and development trend at home and abroad
At present, foreign countries not only do a good job in the basic theory of cryptography , And it has done very well in practical application . A series of specially standardized cryptographic standards have been formulated . Although the collection and discussion of algorithms have been made public , But cryptography is a key technology , All countries will not give up their autonomy and control , Fight for hegemony .
At present, the international community pays great attention to the non mathematical cryptographic theory and technology , The discussion was also very active . Information hiding will play an important role in protecting information from destruction in the future network , Information hiding is a method of hiding confidential information in a large amount of information in the network environment . Especially the image overlay 、 Digital watermark 、 Latent channel 、 The research on the theory and technology of concealment protocol has attracted people's attention .1996 Since then , Many professional seminars on information hiding have been held internationally . The recognition theory and technology based on biometrics have been developed , Formed some theories and technologies , Also formed some products .
1.3 The full text is arranged
This paper consists of six chapters , The full text is arranged as follows :
Chapter one , The introduction . Mainly through some data , Emphasize the importance of research background and significance , The research status of key technologies at home and abroad is introduced . In the age of the Internet , Encryption algorithm is very important to maintain national security 、 Maintaining social peace and development plays an important role .
Chapter two ,DES Algorithm principle . The first part is about the DES Introduction to technology , Then it introduces the working principle and 3DES Algorithm .
The third chapter , be based on 3DES Image encryption program specific implementation . First of all, the processing and grouping of picture data are introduced , Then for intra group encryption and CBC Group operation mode , The operation principle of the program is illustrated in detail , Finally, the feasibility of the method is verified by the ciphertext image display and decryption , The final experimental results are given .
Chapter four , List the problems encountered in the process of programming and give their own solutions .
The fifth chapter , experimental data , The encryption and decryption files and the running effect pictures produced by the final running of the program are given .
Chapter six , summary . The research work done in this paper is summarized .
Chapter vii. , The code implementation of the whole program is given .
Chapter viii. , Give the references cited in the program writing .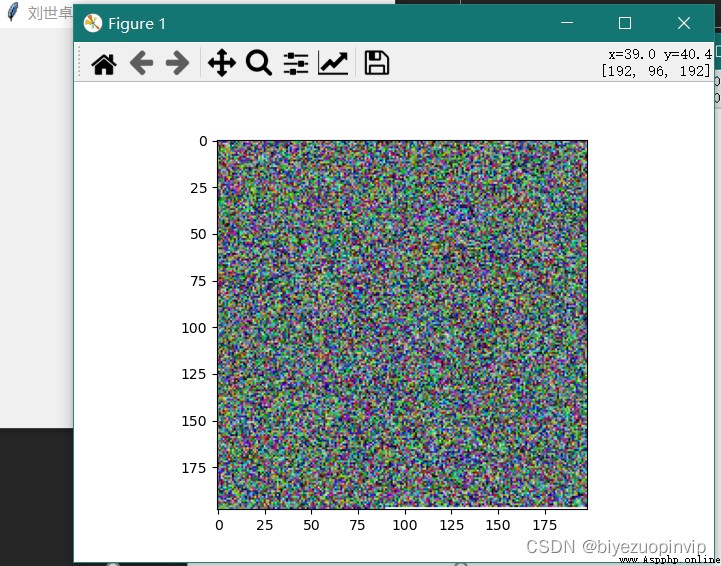
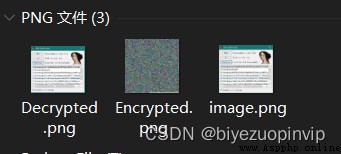
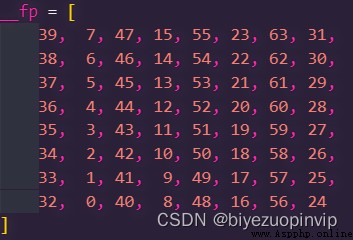

Resource download address :https://download.csdn.net/download/sheziqiong/85730749
Resource download address :https://download.csdn.net/download/sheziqiong/85730749