
author | Junxin
source | About data analysis visualization
I believe that when you capture data , You will encounter many encrypted parameters , Like “token”、“sign” wait , Today, Xiaobian will take you to review these mainstream encryption algorithms in the process of data capture , What are their characteristics 、 What are the encryption methods and so on , Knowing this will help us to reverse crack these encrypted parameters !

The first thing we need to understand is , What is? Encryption and decryption ? seeing the name of a thing one thinks of its function
encryption (Encryption): The process of transforming plaintext data into ciphertext
Decrypt (Decryption): The reverse of encryption , That is, the process of recovering the original plaintext from the ciphertext .
The operation of encryption and decryption algorithms is usually carried out under the control of a set of keys , Become the encryption key respectively (Encryption Key) And decrypt the key (Decryption Key), As shown in the figure below
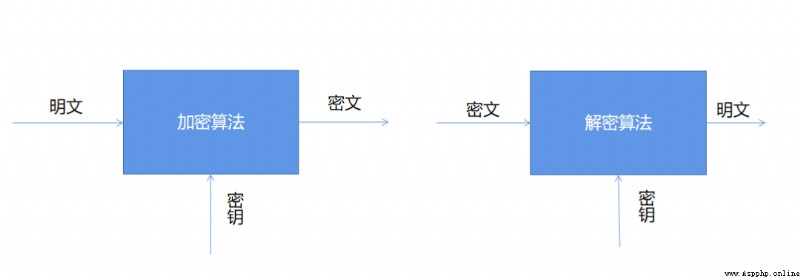
The encryption algorithms are divided into symmetric encryption, asymmetric encryption and hash algorithm , among
Symmetric encryption : That is, the same key is used for encryption and decryption , for example RC4、AES、DES Equal encryption algorithm
Asymmetric encryption : That is, different keys are used for encryption and decryption , for example RSA Encryption algorithm, etc
Hash algorithm : Also known as hash function . Produces a fixed output for input messages of different lengths , The output value is the hash value

Base64 Strictly speaking, it is not an encryption algorithm , Just a way of coding , It is a kind of use 64 Characters , Namely A-Z、a-z、0-9、+、/ this 64 Characters , Realize the coding of data , Can be used in HTTP In the environment, the longer identification information . use Base64 The code is unreadable , It needs to be decoded before reading . We use Python For any web address Base64 The encoding operation of , The code is as follows :
import base64
# Want to encode the string into base64, First convert the string into binary data
url = "www.baidu.com"
bytes_url = url.encode("utf-8")
str_url = base64.b64encode(bytes_url) # The encoded parameter must be binary data
print(str_url)output
b'd3d3LmJhaWR1LmNvbQ=='So again , We can also decode it , The code is as follows :
url = "d3d3LmJhaWR1LmNvbQ=="
str_url = base64.b64decode(url).decode("utf-8")
print(str_url)output
www.baidu.com
MD5 It is a widely used linear hash algorithm , After encryption, a fixed length is generated (32 Bit or 16 position ) The data of , It consists of letters and numbers , Unified case . It finally encrypts the generated data It's irreversible , That is to say, the encrypted data cannot be easily restored to the original string , Except by brute force .
We are Python To realize MD5 encryption :
import hashlib
str = 'this is a md5 demo.'
hl = hashlib.md5()
hl.update(str.encode(encoding='utf-8'))
print('MD5 Before encryption :' + str)
print('MD5 Encrypted as :' + hl.hexdigest())output
MD5 Before encryption :this is a md5 demo.
MD5 Encrypted as :b2caf2a298a9254b38a2e33b75cfbe75As mentioned above , in the light of MD5 Encryption can reduce its security by brute force cracking , Therefore, in the process of practical operation , We will add the salt value (Salt) Or double MD5 Encryption and other methods to increase its reliability , The code is as follows :
# post Incoming parameter
params = "123456"
# The salt value to be spliced after encryption (Salt)
salt = "asdfkjalksdncxvm"
def md5_encrypt():
m = md5()
m.update(params.encode('utf8'))
sign1 = m.hexdigest()
return sign1
def md5_encrypt_with_salt():
m = md5()
m.update((md5_encrypt() + salt).encode('utf8'))
sign2 = m.hexdigest()
return sign2
First, let's talk about DES encryption , The full name is Data Encryption Standard, Data encryption standard , It is a common kind of symmetric encryption , That is, the keys used in the encryption and decryption processes are the same , So if you want to crack it , Through violent enumeration , As long as the computing power is strong enough, it can still be cracked .
AES The full name is Advanced Encryption Standard, yes DES The replacement of algorithm , It is also one of the most popular symmetric encryption algorithms . Want to find out AES Algorithm , First, we have to understand three basic concepts : secret key 、 Fill and pattern .
We have talked a lot about the key before , You can think of it as a key , It can be used for locking , It can be used to unlock .AES Supports three lengths of keys :128 position 、192 Bit and 256 position .
And as for fill The concept of ,AES We need to understand the characteristics of packet encryption , The details are shown in the following figure
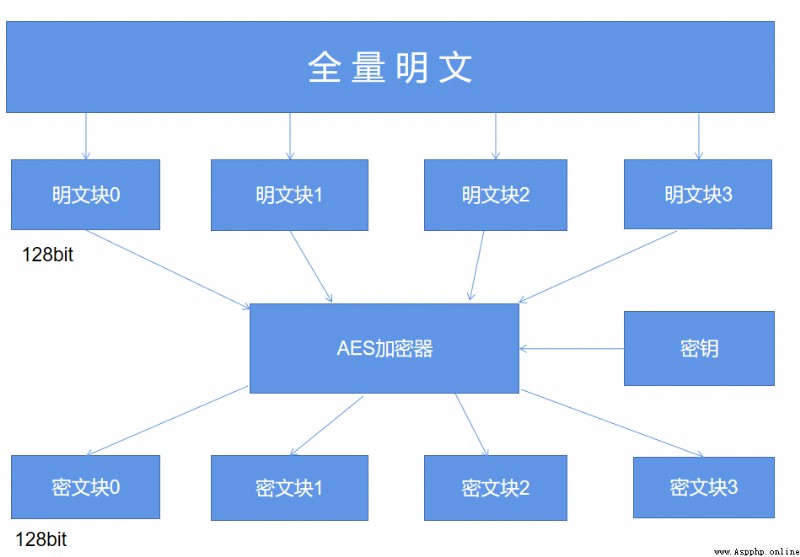
Simply speaking ,AES When the algorithm encrypts plaintext , It is not to encrypt the whole plaintext into a whole ciphertext , Instead, the plaintext is divided into independent plaintext blocks , The length of each plaintext block is 128 The bit .
These plaintext blocks go through AES After the complex processing of the encryptor , Generate independent ciphertext blocks , Putting these ciphertext blocks together is the final AES The result of encryption .
So here's a question , If the length of a plaintext is 196 The bit , If you follow every 128 Bit is a plaintext block to split , The second plaintext block is just 64 Bit , Insufficient 128 What should bit do ? This is the time fill To make a difference , The default fill method is PKCS5Padding as well as ISO10126Padding.
But in the AES When encrypting, a certain filling method is used , The same filling method must be used when decrypting .
AES Working mode of , It is embodied in the process of encrypting plaintext blocks into ciphertext blocks , There are five different working modes , Namely CBC、ECB、CTR、CFB as well as OFB Pattern , similarly , If in AES A certain working mode is used in the encryption process , The same working mode must be adopted for decryption . Finally we use Python Let's do it AES encryption
import base64
from Crypto.Cipher import AES
def AES_encrypt(text, key):
pad = 16 - len(text) % 16
text = text + pad * chr(pad)
text = text.encode("utf-8")
encryptor = AES.new(key.encode('utf-8'), AES.MODE_ECB)
encrypt_text = encryptor.encrypt(text)
encrypt_text = base64.b64encode(encrypt_text)
return encrypt_text.decode('utf-8') Or you can look at other online AES Encryption algorithm implementation process , Basically, they are similar , Due to limited space , Let's stop here for the time being , If you are interested later , I will share the implementation principles and features of other encryption algorithms .

Looking back
Matplotlib Two methods of drawing torus !
13 individual python Necessary knowledge , Recommended collection !
2D Transformation 3D, Look at NVIDIA's AI“ new ” magic !
Get it done Python Several common data structures !
Share
Point collection
A little bit of praise
Click to see