The target site of this blog is 【 Take charge and buy a good house 】 Login page encryption logic , Visit in advance http://eip.chanfine.com/login.jsp Do some interface analysis .
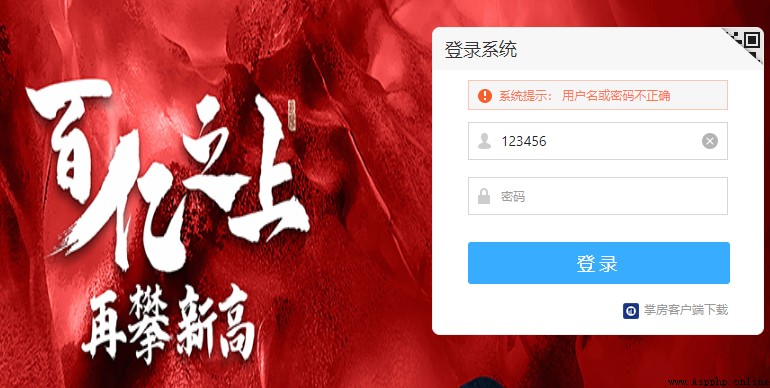
Write an account and password randomly , Test encryption interface .
The interface parameters viewed through the developer tool are as follows .
The encrypted location is shown as follows .
One of the more important things is j_password, The position we want to parse is also here .
Direct global search for keywords j_password You can query the corresponding value .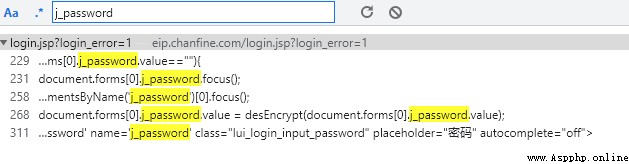
Directly locate in the search results desEncrypt Function position , Get the following .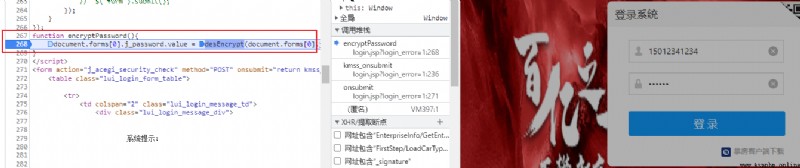
Move the mouse to the encryption function position , Find out VM Related content , Here, we can preliminarily guess that it uses eval Function encryption .
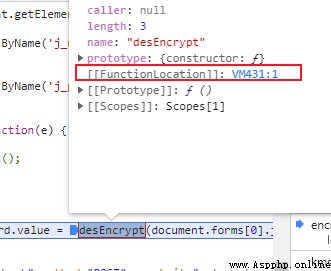
Jump directly to the corresponding code section , In fact, the relevant logic has been obtained , Refer to the following code Python The code can complete the task , But this is the same as when we started learning eval Contrarian contradiction .
function desEncrypt(value, xForm, type) {
if (_0(xForm)) {
return value;
} else {
var keyObj = {
};
if (type == null || "aes" == type.toLowerCase()) {
keyObj = SECURITYKEY.get();
value = CryptoJS.AES.encrypt(value, CryptoJS.enc.Utf8.parse(keyObj.key), {
iv: CryptoJS.enc.Utf8.parse(keyObj.iv),
}).toString();
} else {
keyObj = SECURITYKEY.get("des");
value = CryptoJS.DES.encrypt(value, CryptoJS.enc.Hex.parse(keyObj.key), {
iv: CryptoJS.enc.Hex.parse(keyObj.iv),
});
}
return keyObj.security + value;
}
}
Extract keywords from the above code SECURITYKEY, Retrieve again in the global code .
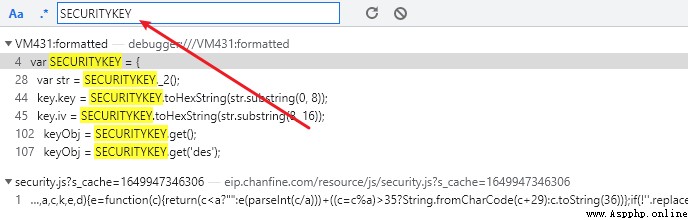
The real location of the encryption function is found in the results , And obviously eval trace .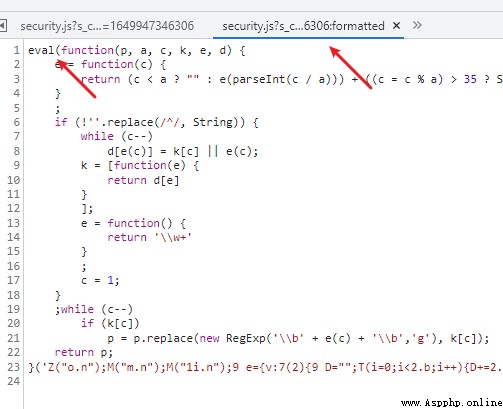
Now that the source of the code has been found , Then you can find an online decryption tool , Just implement the resolution .
You are reading 【 Dream eraser 】 The blog of
Finished reading , You can praise it with a little hand
Find the error , Correct it in the direct comment area
The second part of the eraser 685 Original blog
From the date of order , Case study 5 Guaranteed renewal during the year