近期收到了電子工業出版社贈送的一本網絡安全書籍《python黑帽子》,書中一共24個實驗,今天復現第12個實驗(wordpress文件隱患),我的測試環境是mbp電腦+同事的wordpress在線站點+conda開發環境。wordpress是知名博客網站,如果安裝之後沒有刪除一些配置文件,容易導致網站安全隱患,通過對比在線wordpress和本地wordpress之間的相同文件,得到在線wordpress站點的文件列表~
1、下載最新的wordpress源代碼
2、在mbp上運行腳本
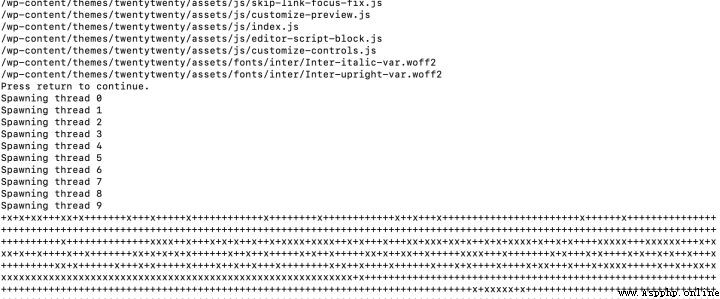
3、得到在線wordpress站點的文件
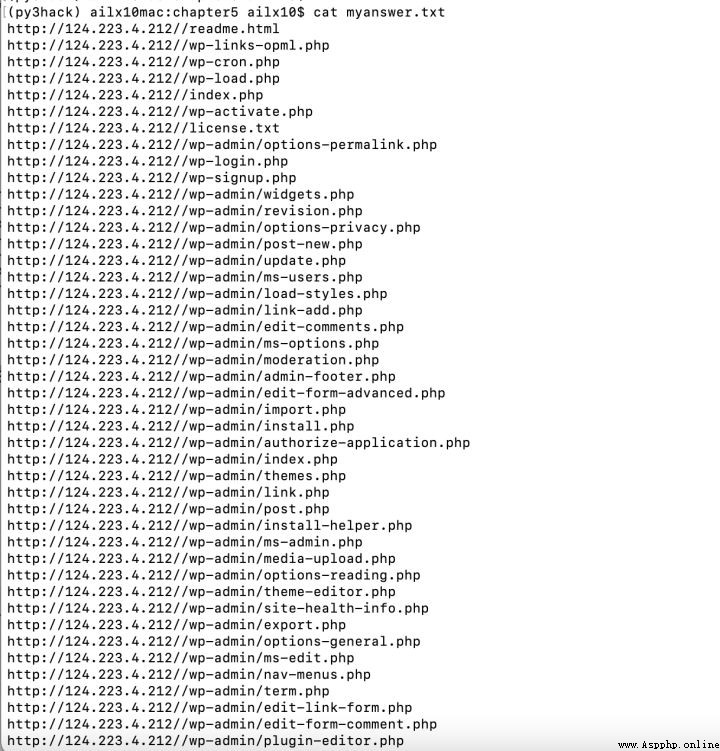
4、嘗試訪問一下
參考代碼:
# -*- coding: utf-8 -*-
# @Time : 2022/6/13 8:21 PM
# @Author : ailx10
# @File : mapper.py
import contextlib
import os
import queue
import requests
import sys
import threading
import time
FILTERED = [".jpg",".gif",".png",".css"]
TARGET = "http://124.223.4.212/"
THREADS = 10
answer = queue.Queue()
web_paths = queue.Queue()
def gather_paths():
for root,_,files in os.walk("."):
for fname in files:
if os.path.splitext(fname)[1] in FILTERED:
continue
path = os.path.join(root,fname)
if path.startswith("."):
path = path[1:]
print(path)
web_paths.put(path)
@contextlib.contextmanager
def chdir(path):
this_dir = os.getcwd()
os.chdir(path)
try:
yield
finally:
os.chdir(this_dir)
def test_remote():
while not web_paths.empty():
path = web_paths.get()
url = f"{TARGET}{path}"
time.sleep(2)
r = requests.get(url)
if r.status_code == 200:
answer.put(url)
sys.stdout.write("+")
else:
sys.stdout.write("x")
sys.stdout.flush()
def run():
mythreads = list()
for i in range(THREADS):
print(f"Spawning thread {i}")
t = threading.Thread(target=test_remote)
mythreads.append(t)
t.start()
for thread in mythreads:
thread.join()
if __name__ == "__main__":
with chdir("/Users/ailx10/py3hack/chapter5/wordpress"):
gather_paths()
input("Press return to continue.")
run()
with open("myanswer.txt","w") as f:
while not answer.empty():
f.write(f"{answer.get()}\n")
print("done.")