實驗環境配置
HOST文件配置如下:
127.0.0.1 app.com
127.0.0.1 sso.com
IIS配置如下:
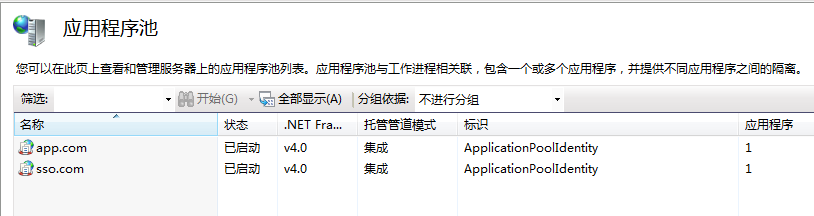
應用程序池采用.Net Framework 4.0
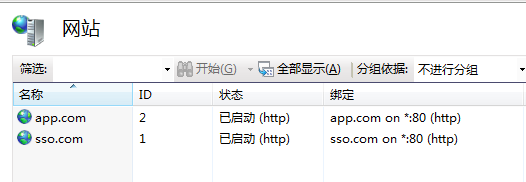
注意IIS綁定的域名,兩個完全不同域的域名。
app.com網站配置如下:
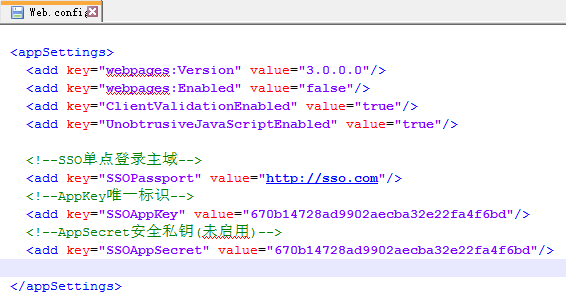
sso.com網站配置如下:
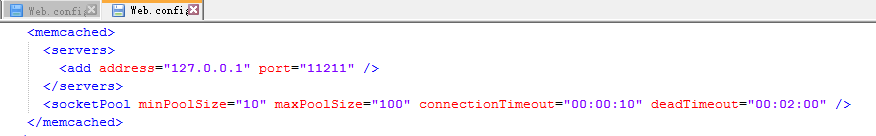
memcached緩存:
數據庫配置:
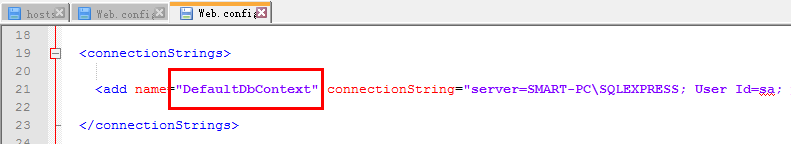
數據庫采用EntityFramework 6.0.0,首次運行會自動創建相應的數據庫和表結構。
授權驗證過程演示:
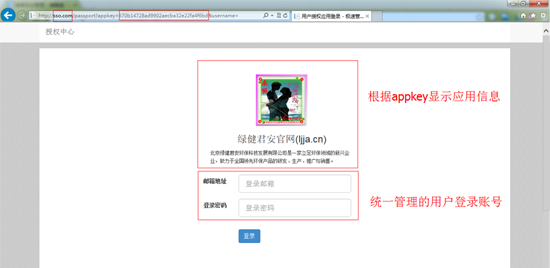
在浏覽器地址欄中訪問:http://app.com,如果用戶還未登陸則網站會自動重定向至:http://sso.com/passport,同時通過QueryString傳參數的方式將對應的AppKey應用標識傳遞過來,運行截圖如下:
URL地址:http://sso.com/passport?appkey=670b14728ad9902aecba32e22fa4f6bd&username=
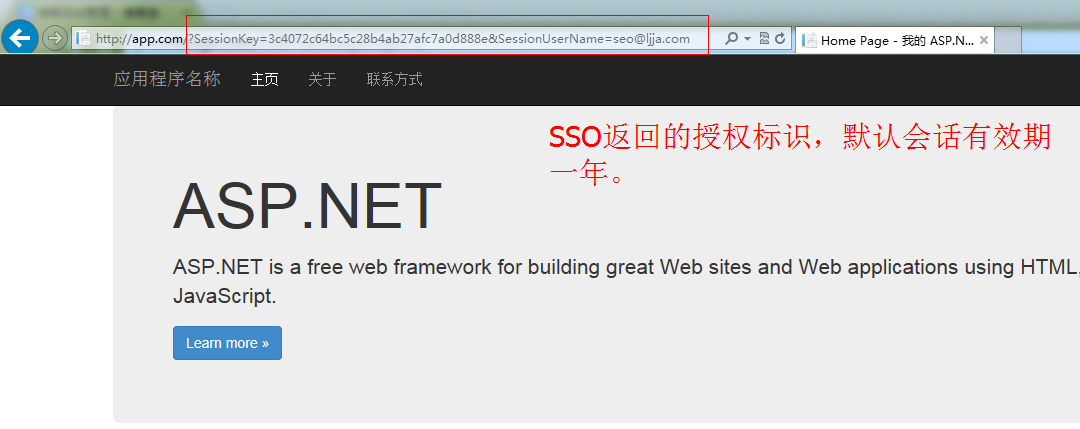
輸入正確的登陸賬號和密碼後,點擊登陸按鈕系統自動301重定向至應用會掉首頁,毀掉成功後如下所示:
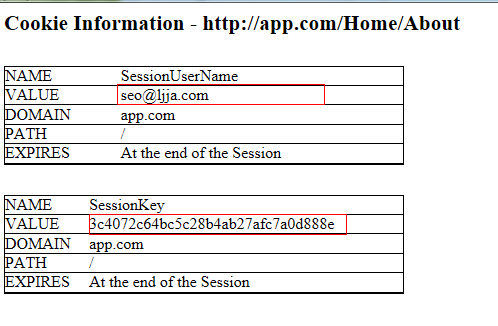
由於在不同的域下進行SSO授權登陸,所以采用QueryString方式返回授權標識。同域網站下可采用Cookie方式。由於301重定向請求是由浏覽器發送的,所以在如果授權標識放入Handers中的話,浏覽器重定向的時候會丟失。重定向成功後,程序自動將授權標識寫入到Cookie中,點擊其他頁面地址時,URL地址欄中將不再會看到授權標示信息。Cookie設置如下:
登陸成功後的後續授權驗證(訪問其他需要授權訪問的頁面):
校驗地址:http://sso.com/api/passport?sessionkey=xxxxxx&remark=xxxxxx
返回結果:true,false
客戶端可以根據實際業務情況,選擇提示用戶授權已丟失,需要重新獲得授權。默認自動重定向至SSO登陸頁面,即:http://sso.com/passport?appkey=670b14728ad9902aecba32e22fa4f6bd&username=seo@ljja.cn 同時登陸頁面郵箱地址文本框會自定補全用戶的登陸賬號,用戶只需輸入登陸密碼即可,授權成功後會話有效期自動延長一年時間。
SSO數據庫驗證日志:
用戶授權驗證日志:
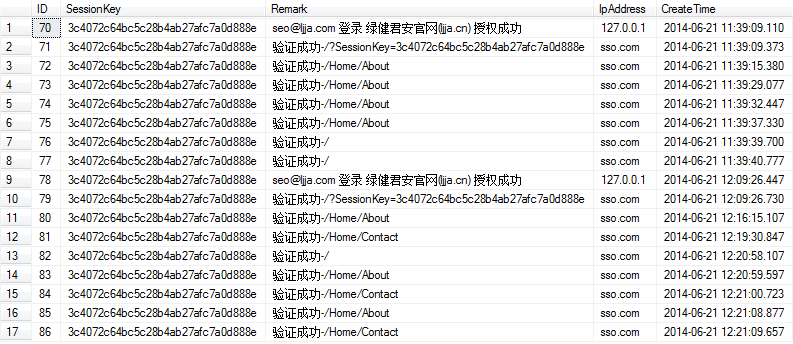
用戶授權會話Session:
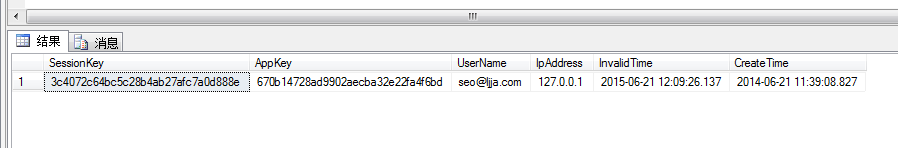
數據庫用戶賬號和應用信息:
應用授權登陸驗證頁面核心代碼:
/// <summary>
/// 公鑰:AppKey
/// 私鑰:AppSecret
/// 會話:SessionKey
/// </summary>
public class PassportController : Controller
{
private readonly IAppInfoService _appInfoService = new AppInfoService();
private readonly IAppUserService _appUserService = new AppUserService();
private readonly IUserAuthSessionService _authSessionService = new UserAuthSessionService();
private readonly IUserAuthOperateService _userAuthOperateService = new UserAuthOperateService();
private const string AppInfo = "AppInfo";
private const string SessionKey = "SessionKey";
private const string SessionUserName = "SessionUserName";
//默認登錄界面
public ActionResult Index(string appKey = "", string username = "")
{
TempData[AppInfo] = _appInfoService.Get(appKey);
var viewModel = new PassportLoginRequest
{
AppKey = appKey,
UserName = username
};
return View(viewModel);
}
//授權登錄
[HttpPost]
public ActionResult Index(PassportLoginRequest model)
{
//獲取應用信息
var appInfo = _appInfoService.Get(model.AppKey);
if (appInfo == null)
{
//應用不存在
return View(model);
}
TempData[AppInfo] = appInfo;
if (ModelState.IsValid == false)
{
//實體驗證失敗
return View(model);
}
//過濾字段無效字符
model.Trim();
//獲取用戶信息
var userInfo = _appUserService.Get(model.UserName);
if (userInfo == null)
{
//用戶不存在
return View(model);
}
if (userInfo.UserPwd != model.Password.ToMd5())
{
//密碼不正確
return View(model);
}
//獲取當前未到期的Session
var currentSession = _authSessionService.ExistsByValid(appInfo.AppKey, userInfo.UserName);
if (currentSession == null)
{
//構建Session
currentSession = new UserAuthSession
{
AppKey = appInfo.AppKey,
CreateTime = DateTime.Now,
InvalidTime = DateTime.Now.AddYears(1),
IpAddress = Request.UserHostAddress,
SessionKey = Guid.NewGuid().ToString().ToMd5(),
UserName = userInfo.UserName
};
//創建Session
_authSessionService.Create(currentSession);
}
else
{
//延長有效期,默認一年
_authSessionService.ExtendValid(currentSession.SessionKey);
}
//記錄用戶授權日志
_userAuthOperateService.Create(new UserAuthOperate
{
CreateTime = DateTime.Now,
IpAddress = Request.UserHostAddress,
Remark = string.Format("{0} 登錄 {1} 授權成功", currentSession.UserName, appInfo.Title),
SessionKey = currentSession.SessionKey
}); 104
var redirectUrl = string.Format("{0}?SessionKey={1}&SessionUserName={2}",
appInfo.ReturnUrl,
currentSession.SessionKey,
userInfo.UserName);
//跳轉默認回調頁面
return Redirect(redirectUrl);
}
}
Memcached會話標識驗證核心代碼:
public class PassportController : ApiController
{
private readonly IUserAuthSessionService _authSessionService = new UserAuthSessionService();
private readonly IUserAuthOperateService _userAuthOperateService = new UserAuthOperateService();
public bool Get(string sessionKey = "", string remark = "")
{
if (_authSessionService.GetCache(sessionKey))
{
_userAuthOperateService.Create(new UserAuthOperate
{
CreateTime = DateTime.Now,
IpAddress = Request.RequestUri.Host,
Remark = string.Format("驗證成功-{0}", remark),
SessionKey = sessionKey
});
return true;
}
_userAuthOperateService.Create(new UserAuthOperate
{
CreateTime = DateTime.Now,
IpAddress = Request.RequestUri.Host,
Remark = string.Format("驗證失敗-{0}", remark),
SessionKey = sessionKey
});
return false;
}
}
Client授權驗證Filters Attribute
public class SSOAuthAttribute : ActionFilterAttribute
{
public const string SessionKey = "SessionKey";
public const string SessionUserName = "SessionUserName";
public override void OnActionExecuting(ActionExecutingContext filterContext)
{
var cookieSessionkey = "";
var cookieSessionUserName = "";
//SessionKey by QueryString
if (filterContext.HttpContext.Request.QueryString[SessionKey] != null)
{
cookieSessionkey = filterContext.HttpContext.Request.QueryString[SessionKey];
filterContext.HttpContext.Response.Cookies.Add(new HttpCookie(SessionKey, cookieSessionkey));
}
//SessionUserName by QueryString
if (filterContext.HttpContext.Request.QueryString[SessionUserName] != null)
{
cookieSessionUserName = filterContext.HttpContext.Request.QueryString[SessionUserName];
filterContext.HttpContext.Response.Cookies.Add(new HttpCookie(SessionUserName, cookieSessionUserName));
}
//從Cookie讀取SessionKey
if (filterContext.HttpContext.Request.Cookies[SessionKey] != null)
{
cookieSessionkey = filterContext.HttpContext.Request.Cookies[SessionKey].Value;
}
//從Cookie讀取SessionUserName
if (filterContext.HttpContext.Request.Cookies[SessionUserName] != null)
{
cookieSessionUserName = filterContext.HttpContext.Request.Cookies[SessionUserName].Value;
}
if (string.IsNullOrEmpty(cookieSessionkey) || string.IsNullOrEmpty(cookieSessionUserName))
{
//直接登錄
filterContext.Result = SsoLoginResult(cookieSessionUserName);
}
else
{
//驗證
if (CheckLogin(cookieSessionkey, filterContext.HttpContext.Request.RawUrl) == false)
{
//會話丟失,跳轉到登錄頁面
filterContext.Result = SsoLoginResult(cookieSessionUserName);
}
}
base.OnActionExecuting(filterContext);
}
public static bool CheckLogin(string sessionKey, string remark = "")
{
var httpClient = new HttpClient
{
BaseAddress = new Uri(ConfigurationManager.AppSettings["SSOPassport"])
};
var requestUri = string.Format("api/Passport?sessionKey={0}&remark={1}", sessionKey, remark);
try
{
var resp = httpClient.GetAsync(requestUri).Result;
resp.EnsureSuccessStatusCode();
return resp.Content.ReadAsAsync<bool>().Result;
}
catch (Exception ex)
{
throw ex;
}
}
private static ActionResult SsoLoginResult(string username)
{
return new RedirectResult(string.Format("{0}/passport?appkey={1}&username={2}",
ConfigurationManager.AppSettings["SSOPassport"],
ConfigurationManager.AppSettings["SSOAppKey"],
username));
}
}
示例SSO驗證特性使用方法:
[SSOAuth]
public class HomeController : Controller
{
public ActionResult Index()
{
return View();
}
public ActionResult About()
{
ViewBag.Message = "Your application description page.";
return View();
}
public ActionResult Contact()
{
ViewBag.Message = "Your contact page.";
return View();
}
}
總結:
從草稿示例代碼中可以看到代碼性能上還有很多優化的地方,還有SSO應用授權登陸頁面的用戶賬號不存在、密碼錯誤等一系列的提示信息等。在業務代碼運行基本正確的後期,可以考慮往更多的安全性層面優化,比如啟用AppSecret私鑰簽名驗證,IP范圍驗證,固定會話請求攻擊、SSO授權登陸界面的驗證碼、會話緩存自動重建、SSo服務器、緩存的水平擴展等。
源碼地址:http://xiazai.jb51.net/201701/yuanma/SmartSSO_jb51.rar
以上就是本文的全部內容,希望對大家的學習有所幫助,也希望大家多多支持幫客之家。